One of the most fundamental aspects in the world of intelligence is the application of a process known as The Intelligence Cycle. It enables intelligence professionals regardless of the area of focus – from Counterterrorism to Cybersecurity – to establish a plan of action and execute on that plan to deliver a high-quality intelligence product to the client.
GroupSense applies the Intelligence Cycle by gathering client requirements, collecting and filtering out the “noise” or irrelevant data, analyzing the risk, and producing a compelling product. We believe that delivering tailored intelligence to our clients facilitates well-informed decisions on the most relevant business and security risks threatening their brand, reputation, employees, infrastructure, and third parties.
What is The Intelligence Cycle?
The Intelligence Cycle is an interactive and iterative process that controls the scope and pace of the overall production of finished intelligence. It consists of five primary steps: planning and direction, collection, processing, analysis and production, and dissemination and feedback.
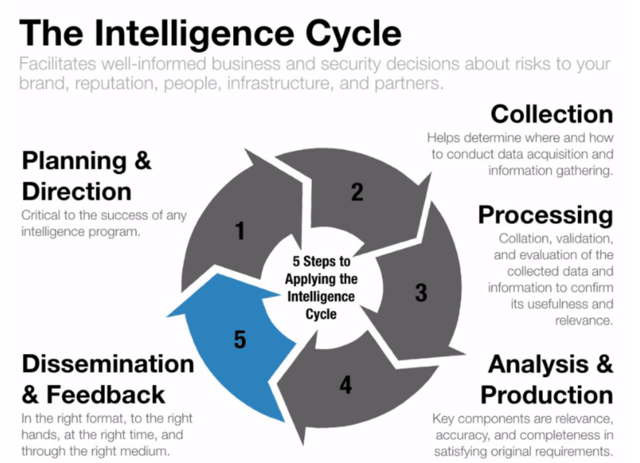
The below represents an abbreviated description of the Intelligence Life Cycle
Planning & Direction: This initial stage is critical to the success of any intelligence program and its application by the decision-making authority that drives the intelligence cycle. It is important to note that proper direction of the intelligence effort is the responsibility of senior management who informs the intelligence team what is needed to satisfy the client’s requirement(s).
Once a clearly defined requirement is obtained the intelligence team can effectively execute by leveraging what they already know about the issue and what they need to find out from available collection resources such as internal telemetry data, honeynet, Surface, Deep, and Dark Web, or community relationships.
Collection: Using the original requirement and devised plan as a guiding force, the collection phase helps you determine where and how you conduct data acquisition and information gathering. If you’re fortunate enough to have a tool such as GroupSense’s proprietary engine – TracelightTM - to aid in the “hunting and gathering” phase, then you would craft a keyword search in the platform and click the “easy” button to retrieve the necessary data and information to answer the client’s requirement(s).
However, as any good intelligence analyst can tell you, there is a wide array of open and closed tools and sources for retrieving the data and information such as Internet research, underground forums, social media, news media, blogs, radio stations, honeynets, telemetry data, internal logs, VirusTotal, Shodan and external relationships.
Processing: The processing step involves the collation, validation, and evaluation of the collected data and information to confirm its usefulness and relevance, a precursor to analysis. The timeliness and accuracy of the processing depend on the type of collected data or information and the type of processing and exploitation system available.
For instance, the processing requirements for data conversion and correlation are different for scraped websites than they would be for system or network logs before they can be intelligible to the human analyst.
By filtering out the “noise” and converting raw data, intelligence professionals can focus on evaluating, analyzing, and interpreting the data and information to produce a finished intelligence product.
Analysis & Production: This is the phase where the intelligence analysts shine by transforming the processed data and information into a fused, complete intelligence product. Through evaluation, analysis, and interpretation, the analysts should produce the finished intelligence in a timely manner and contextualized, easily digestible format that answers the client’s requirement and facilitates their decision-making process.
The key components of this phase are relevance, accuracy, and completeness in satisfying the original requirement, or else you fall into the threat intelligence trap where the deliverable is interesting but not compelling enough to act, wasting both parties' time and resources. This cannot be stressed enough since repeating this mistake too often, you’ll eventually learn through churn.
Dissemination & Feedback: In this final step, the intelligence team employs what I call the four “rights” rule: delivered in the “right” format, placed in the “right” hands, given at the “right” time, and provided through the “right” medium. These elements are important because the product is only valuable if it is delivered in a timely fashion in an appropriate medium and meets - preferably exceeds - the client’s requirement.
As a closed loop system, the intelligence cycle ends when the originator of the request provides feedback as to the value of the product. Feedback can be provided via dialogue in a ticketing system, email correspondence, phone call, video conferencing, or an in-person meeting.
The Intelligence Cycle in Action: A Case Study
A popular e-Commerce company is facing a continual threat of phishing emails and credential harvesting websites originating from threat actors mimicking their brand’s domain name and official customer login page. Recognizing the need for enhanced detection, alerting, and remediation of the issue, they seek external vendor support.
As a reputable managed threat intelligence provider, GroupSense is hired to serve as an extension of the client’s security team and help them protect their brand from typosquatting and phishing threats. During the initial engagement, GroupSense collaborates with the client to better understand their business need, develop intelligence requirements, and formulate an intelligence collection plan (Planning & Direction).
Using the collection plan, GroupSense analysts establish alerting criteria in Tracelight™ to detect newly registered domains (NRDs) (Collection). Additionally, they perform keyword searches in Tracelight™ to retrieve all actively registered domain name variants and phishing campaigns targeting the client, their partners, and their customers (Collection).
On Day 1, GroupSense receives an automated alerted of NRDs and previously created domains (newly observed domains) mimicking the client’s brand (Processing). The intelligence team uses these domains as "seed" data to further enrich it using Tracelight™ by gathering Whois information, retrieving the hosted website’s HTML code and taking a screenshot, obtaining the SSL certificate, the IP address resolution, and performing reverse lookup data i.e. reverse Whois, Passive DNS, etc. (Analysis).
After filtering out false positives and non-credible threats, the lead analyst writes their findings into an intelligence report to include recommended actions on minimizing the client’s risk exposure via our internal dissemination system (Dissemination).
Once the customer reviews the report, they confirm the threat and request GroupSense initiates a domain take-down (Feedback). The team acknowledges the request and initiates the domain take-down process (Feedback).
Upon deletion of the offender domain by the Registrar, GroupSense re-engages the client to inform them about the neutralization of the threat.
Subscribe to our blog to stay updated
Conclusion
In this blog, we briefly introduced The Intelligence Cycle and the vital role that it plays in delivering insightful, actionable intelligence that satisfies the client’s intelligence need. Implementing this process ensures intelligence professionals remain within the scope of the client’s requirements, allowing them to proactively deliver finished intelligence to clients to help them strengthen their risk posture.




