GroupSense performed a deep and dark web investigation into the critical remote code execution (RCE) zero-day impacting the Apache Java-based logging utility Log4j (CVE-2021-44228). This high severity vulnerability is already being actively exploited in the wild, per numerous public reports. The attack vector is extremely trivial for threat actors to exploit, requiring only a single string of code, and impacts software products from numerous vendors. The US Cybersecurity and Infrastructure Security Agency is maintaining an updated list of affected vendors.
GroupSense has observed extensive discussion among threat actors regarding the log4j/Log4Shell vulnerability.
Malware Offers
On 13-14 December 2021, Threat Actor 1 posted samples of malware that the account owners claim is designed to exploit log4j on their large Telegram channel (Figure 1). One sample was posted in response to a request from a channel member. In Russian, the channel description claims that the threat actors own “the largest collection of malware source code, virus samples, and articles on the Internet,” which they appear to host on a separate dark web site (available in both English and Russian). GroupSense has not yet analyzed the offered malware samples, but assesses with moderate confidence that the offer is legitimate given the channel’s large community (4,793 subscribers) and prior activity we have observed on the channel.
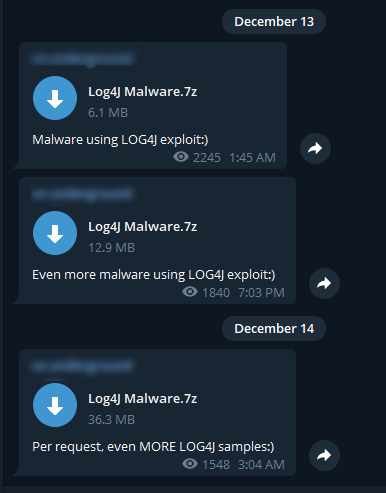
Figure 1: Malware offers exploiting log4j posted to a threat actor’s Telegram channel
Exploitation Chatter
GroupSense has observed considerable chatter regarding log4j exploits on popular dark web forums. An example discussion can be seen in a RaidForums thread created on 10 December 2021 (Figure 2). The initial post, created by Threat Actor 2, simply discussed CVE-2021-44228 and likely used information gleaned from public reporting on the vulnerability. Within minutes of the post, two prominent threat actors, Threat Actor 3 and Threat Actor 4, joined the discussion, claiming they used the exploit on multiple targets already (Figure 3). Both responding threat actors have high reputation scores on the forum, lending some measure of legitimacy to their claims.
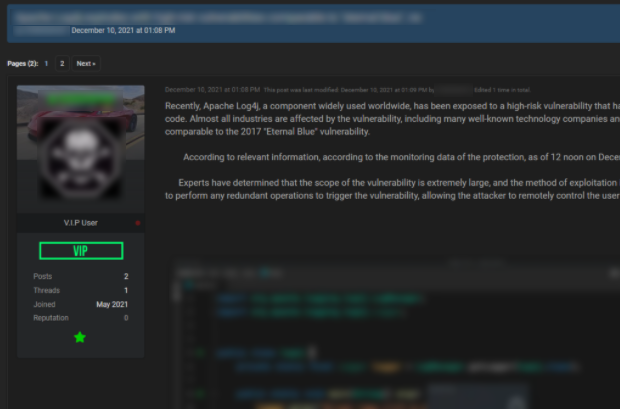
Figure 2: Threat Actor 2’s initial Raidforums post about log4j
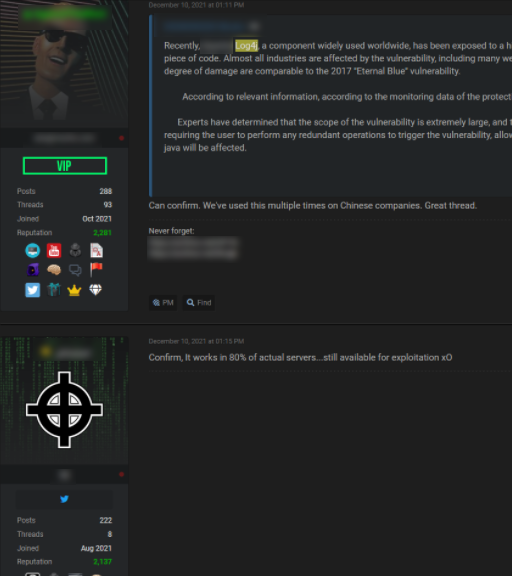
Figure 3: Two prominent threat actors confirm efficacy of exploiting log4j
On 11 December 2021, threat actor PwnSec replied to the thread with a link to a log4j exploit proof-of-concept on Github (Figure 4). This actor was further observed sharing the PoC in their Telegram channel PWND! Unethical Hackerz, where they encouraged their subscribers to utilize it.
Figure 4: Log4j exploit proof-of-concept shared by PwnSec
Additionally, GroupSense observed chatter demonstrating tests of log4j exploits. Posts shared from PWND! Unethical Hackerz and shared in the Telegram channel PWND! Community Group contained screenshots on various sites and programs, including Minecraft (Figure 5). The involved threat actors appear to have used a DNS logger to probe the vulnerability.
Figure 5: Threat actor probing Minecraft for log4j vulnerability, seemingly with the use of a DNS logger.
GroupSense also observed chatter surrounding log4j on a clear web Chinese-language cybersecurity forum where pentesting tutorials, resources, and general hacking knowledge are exchanged. A post shared by Threat Actor 5 on the forum contains screenshots of a user testing the exploit on their own system. Notably, the post includes no mention of the Java Naming and Directory Interface (JNDI). A call to JNDI has been a standard component of Log4Shell exploitation code observed among threat actors by GroupSense. GroupSense assesses with moderate confidence that the exploit in the tutorial is a different remote code execution exploit that is unrelated to log4j.
The tutorial ends with a screenshot of a search query on FOFA.so, a search engine that can be described as the Chinese-language equivalent of Shodan (Figure 6).
A previous thread created by Threat Actor 5 included a tutorial on bypassing antivirus software, with one section titled “Denial of Responsibility and Other Nonsense.” This section states: “The source code is for learning only, don't use it for other purposes. For other purposes, please delete and modify by yourself.” One user replied with “good idea” and another user commented “Gives an idea…” Threat Actor 5 does not appear to be malicious. However, their tutorials on log4j and bypassing antivirus software may be picked up by visitors and potentially shared with threat actors seeking to exploit log4j.
Figure 6: Threat Actor 5 ends their log4j tutorial with a search query on the FOFA search engine.
GroupSense also observed threat actors discussing the use of the log4j vulnerability to steal cryptocurrency. On 11 December 2021, a threat actor on the Japanese-language dark web forum posted about hypothetically using the vulnerability to steal from Java-based crypto wallets (Figure 7). Threat Actor 6 added the caveat that they do not know if such wallets exist. The following day, another threat actor, Threat Actor 7, on the forum claimed to have successfully exploited the vulnerability using a worm to access a website and steal a private bitcoin key (Figure 8).
Figure 7: Threat Actor 6 suggests using the log4j vulnerability to steal from crypto wallets on a Japanese-language forum.
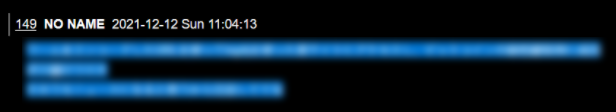
Figure 8: Threat Actor 7 claims to have successfully exploited log4j with a worm in order to steal a private bitcoin key.
GroupSense also identified threat actors sharing proof-of-concepts for log4j exploits. On 16 December 2021, threat actor C47 shared two PoCs in a log4j discussion thread on the dark web forum Exploit (Figure 9). The actor noted that they had not tested the exploits. The exploits were shared from 0Day Today (also known as Inj3ct0r), a deep web database of exploits and vulnerabilities. The two exploits were posted on the site on 14 December 2021 (Figure 10)
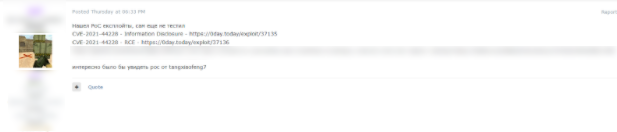
Figure 9: Exploit post by C47 sharing log4j exploits.
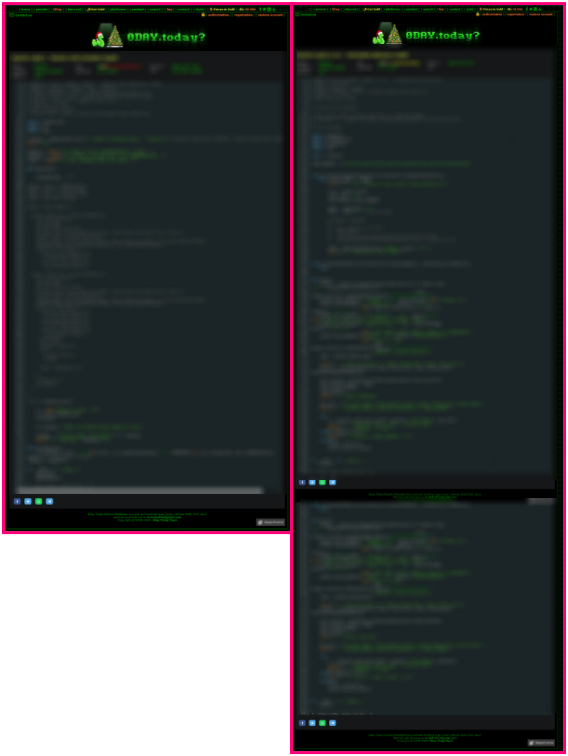
Figure 10: Two log4j exploits on 0Day.Today that were shared on Exploit
Vulnerability Scanning and Security Bypasses
GroupSense has observed active discussion and sharing of vulnerability scanners and security bypassess among threat actors interested in exploiting log4j. For example, on 14 December 2021, Threat Actor 8 shared a scanner targeted at vulnerable log4j hosts on Raidforums (Figure 11). The code is shared from an encrypted GitHub link, with Threat Actor 8 offering the password. Threat Actor 8 purports that this scanner can bypass firewalls.
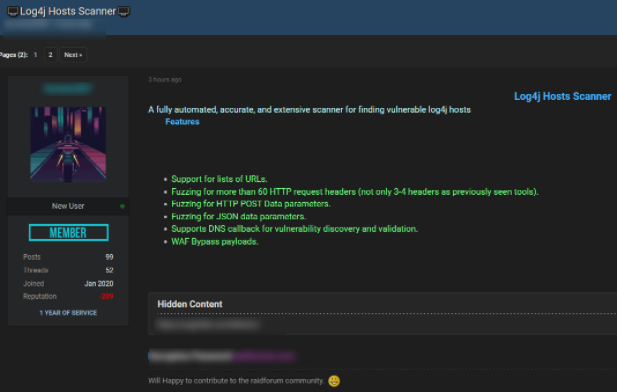
Figure 11: Threat Actor 8 offers a log4j vulnerability scanner on Raidforums.
GroupSense also observed discussion of firewall-bypassing scanners on the prominent forum XSS. On 14 December 2021, Threat Actor 9 posted a log4j scanner that functions as a plugin for Burp, a penetration testing software (Figure 12). The threat actor claims that the scanner provides synchronous and asynchronous detection, hostname and username detection and an ability for single-issue scan. Threat Actor 9 compares it to ActionScan ++, which can only perform the former.
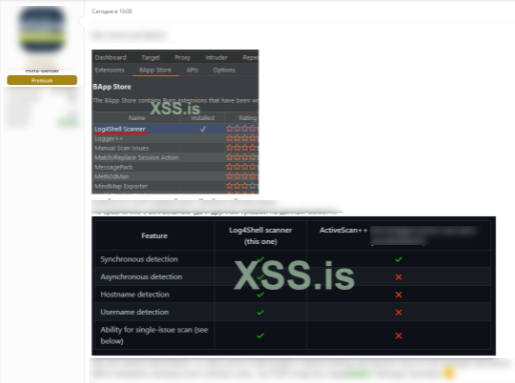
Figure 12: log4j scanner posted to XSS by Threat Actor 9, with comparison to ActiveScan++
Actors have also created log4j scanners employing Google Dorks. On 20 December 2021, GitHub user JagarYousef created a GitHub repository with instructions and code for developing a Python-based scanner that can detect files affected by Log4Shell (Figure 13). The actor claims to be providing the scanner for educational and demonstration purposes, and declares that they are not responsible for potential malicious use of the tool.
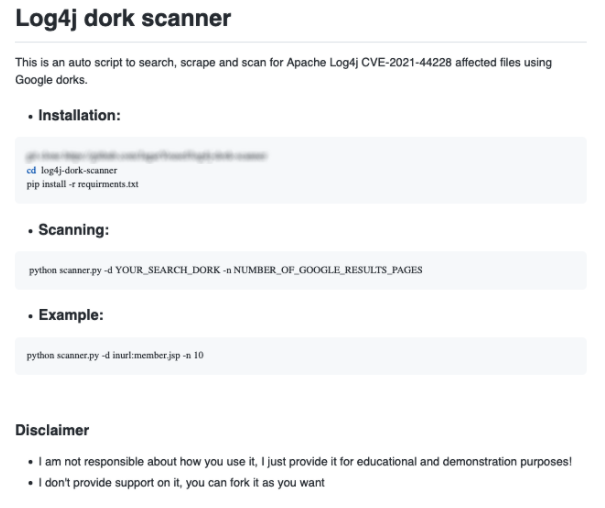
Figure 13: Google Dork log4j scanner
Threat actors are also interested in firewall bypasses for direct exploitation. On 12 December 2021, Threat Actor 10 posted sample code to bypass Cloudflare security solutions to an XSS thread about exploiting log4j (Figure 14). Cloudflare security teams first observed log4j exploitation on 1 December 2021, nine days before public disclosure of CVE-2021-44228 and the earliest exploit of the vulnerability announced so far.
Figure 14: Cloudflare bypass for log4j exploitation shared by Threat Actor 10 on XSS
In the same thread, Threat Actor 11 added a list of web-application firewall (WAF) bypasses (Figure 15). GroupSense observed similar lists of bypasses on multiple XSS threads.
Figure 15: List of firewall bypasses provided by weaver.
Recommendations
GroupSense recommends clients immediately update impacted servers with Apache Log4j to version 2.17.1. Prior fixes in versions 2.15.0 through 2.17.0 do not fully fix all recently-discovered vulnerabilities pertaining to Apache Log4j. This is an active, evolving incident. Please remain vigilant, continue tracking Apache updates and other vendor support pages regularly.