Background
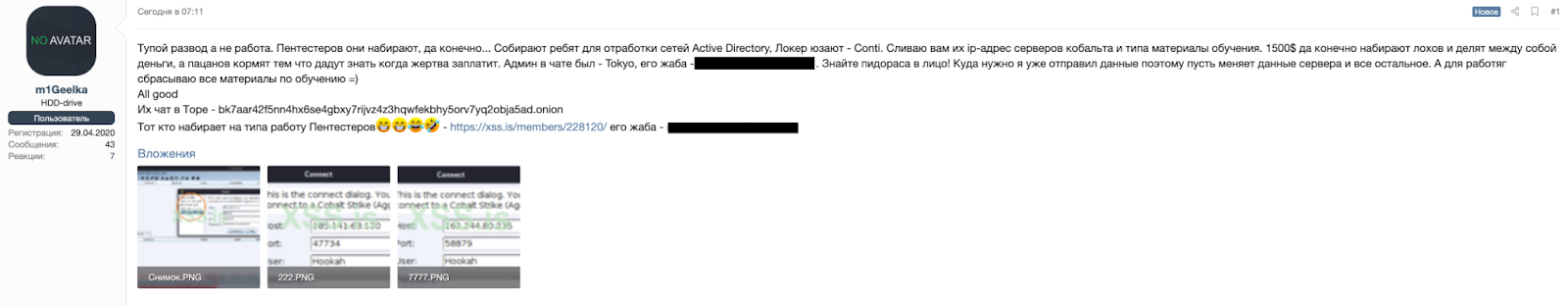
On 5 August 2021, a seemingly disgruntled Russian-speaking threat actor claiming to work as an affiliate for the popular ransomware group Conti leaked on the underground forum XSS a 113 MB archive of training materials and tools allegedly used by Conti to conduct its ransomware attacks (Figure 1).
The actor, using the alias m1Geelka, claimed Conti underpays its penetration testers at just $1,500 an attack, while the core of the group reap much larger earnings for themselves. In addition to the leaked materials, m1Geelka also published contact information of two Conti operators and four IP addresses of Conti command & control (C2) servers. m1Geelka also stated that unlike Conti, other Ransomware-as-a-Service (RaaS) groups treat their employees “honestly” and listed two other groups, Cl0p and REvil, as examples.
Figure 1: Initial post by m1Geelka on the forum XSS [contact information redacted by GroupSense]
Ransomware Group’s Vacancy Announcement: Evening Shift, Monday thru Friday. Paid Holidays.
While GroupSense has been unable to independently corroborate whether m1Geelka was affiliated with Conti, we assess with moderate confidence that the extensive details in the leaked materials, coupled with the actor’s previous messages make m1Geelka a credible source. We believe the leaked materials are genuine and provide a valuable behind-the-scenes look at how ransomware groups operate.
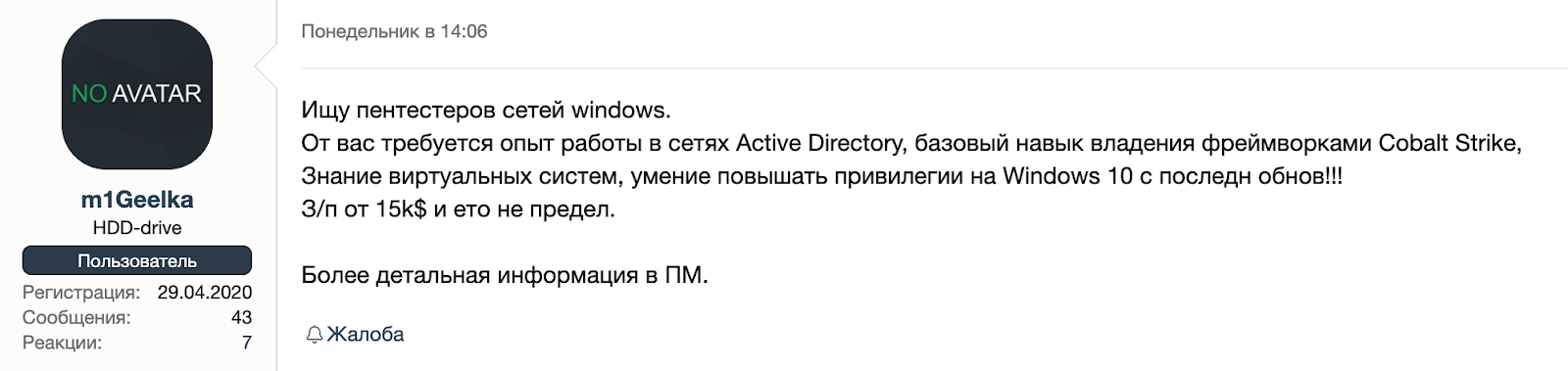
- m1Geelka has been active on the XSS forum since April 2020, and in the days prior to the 5 August leak, the actor posted messages on the forum recruiting pen testers with experience in Windows networks (Figure 2).
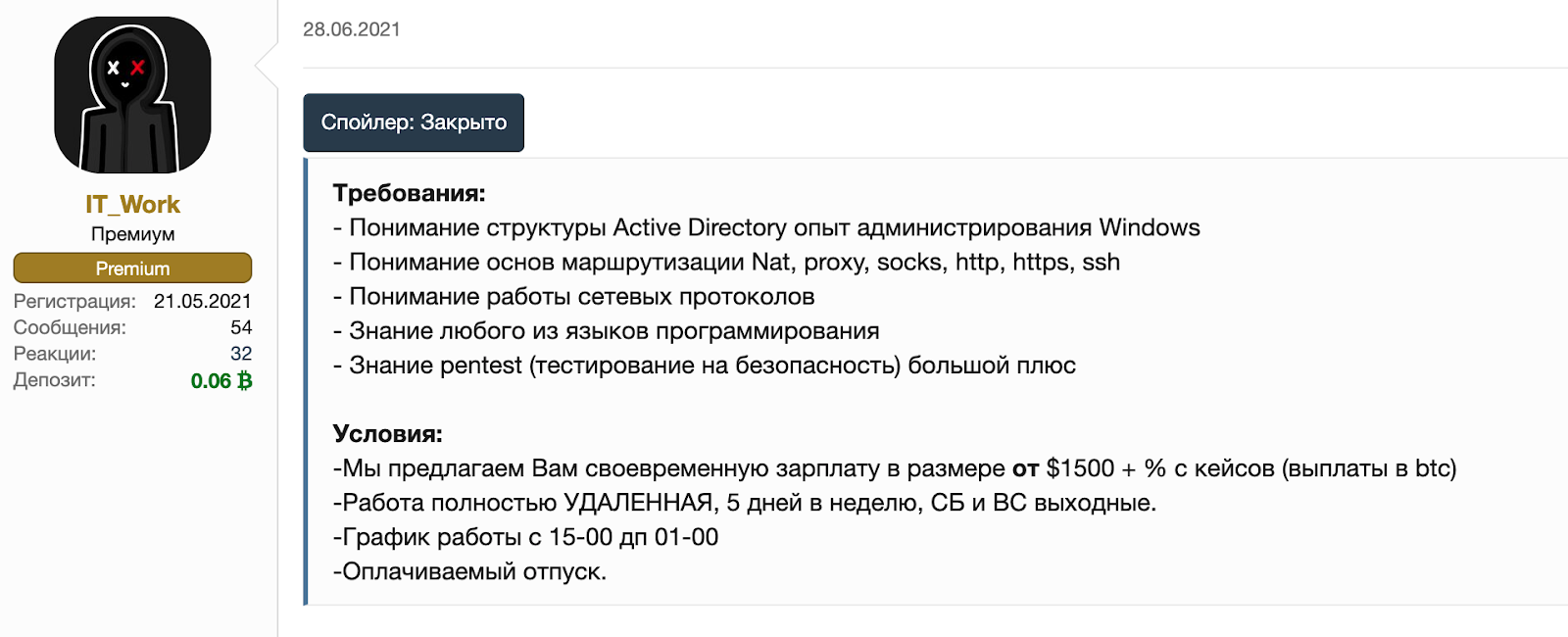
- In the 5 August post complaining about Conti’s activities, m1Geelka also pointed to the recruitment efforts of a separate XSS forum user, IT_work, who had in previous months posted messages recruiting for penetration testers and also offering payment upwards of $1,500 (Figure 3). We surmise that IT_Work is a recruiter for Conti or another similar ransomware group. The requirements shed some light on how these groups’ structure emulates legitimate business: the vacancy announcement states “The work is 5 days a week with weekends off, with a schedule from 3:00 pm to 1:00 am. Paid holidays.”
Training Material Sheds Light Into Ransomware Operators’ Playbook
Tools
The leaked training materials, written in Russian, show the tactics, techniques, and procedures used by the group. We note that the materials make frequent references to the popular penetration testing tool Cobalt Strike. In addition, the manuals discuss the following tools:
- Metasploit: A penetration testing framework
- Mimikatz: One of the most powerful password harvesting tools in existence
- Armitage: A visualization tool for Metasploit
- PowerView: a series of functions that performs network and Windows domain enumeration and exploitation.
- PowerUpSQL: A PowerShell Toolkit for Attacking SQL Server
- AnyDesk: A remote desktop application
- Rclone: Used for exfiltration; provides an easy and effective way of copying data to an array of cloud storage providers.
Tactics, Techniques, and Procedures (TTPs)
Some of the training documents briefly discuss how to maintain anonymity. One document states that the “task is not to hide (as it does not work), but rather to merge with the crowd” The material advises the threat actors not to disable features such as Javascript, Flash, as it will draw more attention. A separate document advocates for the use of Whonix, a privacy oriented Debian Linux operating system that forces communications through the Tor network.
The actors also list a small number of common passwords and password patterns that are often encountered in corporate environments. They list the following passwords:
- Password1
- Hello123
- password
- Welcome1
- banco@1
- training
- Password123
- job12345
- spring
- Food1234
- June2020
- July2020
- August20
- August2020
- Summer20
- Summer2020
- June2020!
- July2020!
- August20!
- August2020!
- Summer20!
- Summer2020!”
Another training document states that after escalating privileges and finding the admin’s domain, Cobalt Strike should be launched. The training manual states “We are interested in: financial documents,accounting, I.T., clients, projects, and so forth. It all depends on what line of business our target is in.”
The threat actors also recommend changing the RDP (Remote Desktop Protocol) port to 1350 TCP/UDP.
They discuss escalating privileges to a server with Shadow Protext SPX (StorageCraft). StorageCraft ShadowProtect SPX is a backup and disaster recovery product.
We also observed one file discussing the exploitation of CVE-2020-1472 Zerologon (https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-1472)
Threat Group has Potential Ties to Ukraine
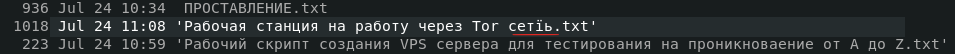
While the leaked manuals are all in Russian, GroupSense observed that one of the words in a filename is not in Russian (Figure 4). Instead, the word “сетïь” shows up as Serbian, according to Google translate. However, it is more likely that this is a typo from a Ukrainian keyboard as the double dotted ï is prominent in the Ukrainian language. Ukrainians frequently converse in both Russian and Ukrainian.
Recommendations
GroupSense recommends avoiding common mistakes that can enable ransomware groups from gaining a foothold into your network. For example, the simple passwords highlighted in the leaked training manuals should not meet the minimum enterprise password requirements. System administrators should also set up rules in place to monitor for unusual activity, paying close attention to the tools highlighted above. GroupSense offers additional ransomware services and mitigation guidelines, available at groupsense.io.