Ransomware needs its own kill chain framework
GroupSense's Intelligence Analyst, Nicole Hoffman, is featured in SC Media. Nicole explains the evolution of the Cyber Kill Chain developed by Lockheed Martin and argues that the industry needs a kill chain specifically for ransomware.
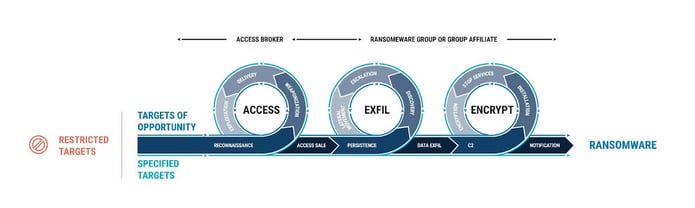
Figure 1: Ransomware Kill Chain Graphic (click to enlarge)
In her article, Nicole talks about the evolution of the Kill Chain, ransomware's threat scenario, how to disrupt the Ransomware Kill Chain and about what's beyond the Kill Chain. Below is an excerpt from the SC Media article:
"Security teams also have a considerable amount of work before and after the kill chain. Before, organizations should take steps to minimize the opportunities for threat actors to establish access. For example, the most common attack vectors used to carry out ransomware attacks are phishing campaigns, remote desktop protocol (RDP) vulnerabilities, and software vulnerabilities. Addressing these important issues could substantially reduce the number of soft targets for threat actors.
Likewise, companies should properly prepare for a ransomware attack. Generic incident response plans will not get the job done – security teams need to have a specialized ransomware response plan in place where executives and third parties have engaged in tabletop exercises and know exactly what needs to happen. Companies should discuss issues like “should we pay ransom or not?” ahead of time, and if the company opts to pay, it needs to assign a predefined (and competent) representative to handle the negotiation and transaction with the threat actor."