Republished from October 2019
Last week I was asked by one of the 24-hour news networks to comment on camera about Jared Kushner’s use of WhatsApp for official White House business. The news network wanted my thoughts on the vulnerabilities and risks associated with this behavior. My first thought was that this was outside the core focus of what we do at GroupSense, but before I declined I gathered my thoughts on the topic. I quickly realized that this falls squarely in line with the GroupSense mission. Since the networks only want sound bites, I thought I would crystalize the concerns with greater context here. It is my intention to make this post apolitical, but in today’s climate, people are likely to trigger on the particular individual, so replace “Mr. Kushner” with “WH Staffer with critical national intelligence information”, and the risks remain.
First, let’s review the primary concerns around using WhatsApp for official White House business, especially for national security related conversations.
- Metadata. Metadata exposes who’s talking, when, how long and where. Message data stored at rest in world-wide data centers.
- The WhatsApp legal agreement. When a user downloads and signs up for WhatsApp, they are agreeing to a legal contract. What does that agreement allow WhatsApp to do with that data?
- Screen captures and emails make this worse. When you screen-capture something on your phone, where does that picture go? You can easily email screen captures to document some incident or comment ... email is fine for sending top secret and national security information, right?
- Mobile phones themselves are vulnerable. Device security. Whether it’s an iPhone or Android device, it is still a computer.
-
The real vulnerability: Humans
The Metadata
Let’s start with metadata. While WhatsApp is allegedly encrypted end to end, metadata about conversations is collected. WhatsApp spells out what they collect in their Privacy Policy. (Have you read it? Really read it?) WhatsApp categorizes information they collect into three categories: Information the user provides, information they automatically collect, and information provided by third parties. I have highlighted the data I think could have an impact on national security, leaving the third party list alone due to its subjective nature. Here is the list:
Information you provide
- Your account information
- Your messages
- Your connections
- Customer support
Automatically Collected Information
- Usage and log information
- Transactional information
- Device and connection information
- Cookies
- Status information
Third-Party Information
- Information others provide about you
- Third-party providers
- Third-party services
It is clear that WhatsApp is collecting information about their users which could provide insight into policy, connections, conversation participants, frequency and even geolocation data. Some of this data we could classify as metadata and some of it is frankly just data - but valuable data nonetheless. As many of you know, the NSA built an entire intelligence operation around metadata!
A quick look at the WhatsApp permissions on an iPhone indicates the default permissions allow access to some pretty important stuff.
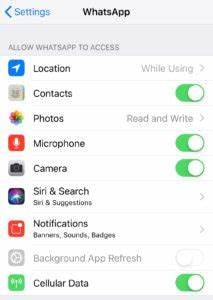
Yes, this data is in the hands of WhatsApp and likely not resident on the user’s device. WhatsApp is “a member of the Facebook family of companies” and let’s be honest here - Facebook has problems with both security and credibility.
The WhatsApp Legal Agreement
We'll move on to the general legal concerns, but remember I AM NOT A LAWYER. (Sorry to yell, but want to make sure you heard me.)
I am sure the White House counsel and Mr. Kushner’s own attorneys have considered this, but it is important to recognize that when anyone uses WhatsApp, they agree to a contract, a legal contract with many implications. While I applaud WhatsApp for using mostly common English language, there are plenty of things to be concerned about.
“You must access and use our Services only for legal, authorized, and acceptable purposes.”
I am not going to weigh in on whether using WhatsApp for official White House business is violating the law, but right off the bat we have a potential issue.
“You agree to our data practices, including the collection, use, processing, and sharing of your information as described in our Privacy Policy, as well as the transfer and processing of your information to the United States and other countries globally where we have or use facilities, service providers, or partners, regardless of where you use our Services.”
This allows WhatsApp to not only collect metadata, but to distribute it as they see necessary or are compelled by law. Those laws could differ in China or the European Union. This also highlights the truth that the metadata collected doesn't just reside in a data center in Santa Clara, but wherever WhatsApp has decided to replicate that data, anywhere in the world.
There are broader implications here; while I don’t have direct knowledge of WhatsApp’s cloud infrastructure, it is common for large service providers, including Facebook and Google, to outsource data center capacity to third parties. Those third parties are likely upstanding businesses, but in foreign countries can be under the purview of the government or business interests.
“You are responsible for keeping your device and your WhatsApp account safe and secure,”
WhatsApp is making a fair point here, we will get to this later.
“...you may choose to use third-party data backup services (such as iCloud or Google Drive) that are integrated with our Services or interact with a share button on a third party’s website that enables you to send information to your WhatsApp contacts. Please note that when you use third-party services, their own terms and privacy policies will govern your use of those services.”
This opens a can of worms around third party terms and conditions, plus the possibility of data replication to other apps. Replication is an issue I will touch on later, but could WhatsApp conversations be backed up to third party services in an unencrypted fashion?
This next part is the obligatory “your data is my data” social media clause.
“In order to operate and provide our Services, you grant WhatsApp a worldwide, non-exclusive, royalty-free, sub-licensable, and transferable license to use, reproduce, distribute, create derivative works of, display, and perform the information (including the content) that you upload, submit, store, send, or receive on or through our Services. The rights you grant in this license are for the limited purpose of operating and providing our Services (such as to allow us to display your profile picture and status message, transmit your messages, store your undelivered messages on our servers for up to 30 days as we try to deliver them, and otherwise as described in our Privacy Policy).”
We know regular WhatsApp messages are encrypted end to end, so here they are likely referring to anything outside the encrypted message, which includes the metadata referenced above, any status messages, profile information, profile photos, etc.
Technically, it seems it would also apply to the messages themselves, encrypted or otherwise. These messages are apparently being buffered for transmission - buffered where? Santa Clara? Tokyo? All the WhatsApp data centers world-wide? Could potentially sensitive national security related information be stored on foreign data centers? It is unlikely a foreign government or influencer would go to the trouble to attempt to decrypt ciphertext generated from a conversation between my friend in Mexico City and I, but far more likely they would go to the effort for a top White House staffer. (It would be difficult - but not impossible - to decrypt, as the key generation is solid and the Open Whisper Systems AKA Signal Protocol employed by WhatsApp uses AES256 to create the ciphertext and HMAC-SHA256 for message authentication.)
Screen captures and emails make this worse
One of the concerns that arose from the use of private devices and communications tools was the need to comply with the Federal Records Act and Title 18 requirements around record-keeping and the safeguarding of classified documents. (Think Hillary Clinton’s email server.) The use of a private device and a third-party application such as WhatsApp could be in direct conflict with those rules. The attorney representing Kushner responded that Kushner had taken screen shots of the relevant conversations and forwarded those to his White House email address in order to comply with record-keeping laws.
Where to start? When I take a screenshot of something on my phone, it goes into my photos. My photos are synced with iCloud. Does Mr. Kushner sync his phone to iCloud? iTunes? Google? Where is that data now?
We don’t know what level of encryption Mr. Kushner is utilizing for email communications from his phone to the White House. Let’s hope it is the best a nation-state can provide, otherwise he is circumventing the security of WhatsApp altogether and sending those critical messages unencrypted over the internet. *Fingers Crossed*
Mobile phones themselves are vulnerable
During my interview I was asked “...if you were going to attack WhatsApp to get to Kushner’s communication data, how would you do it?” To which I responded “...I wouldn’t attack WhatsApp.”
I wouldn’t, that’s the truth, because I would attack the endpoint. WhatsApp encrypts data end to end, which would make it difficult to intercept and decrypt in transit. If I had access to the endpoint, however, that’s an entirely different game. The largest vulnerabilities related to this behavior are the phones of Mr. Kushner and whomever he is communicating with. These phones’ operating systems are susceptible to attack and are constantly connected to the internet. The weakest link is the phone itself.
Imagine another scenario where a threat actor is able to take control of Mr. Kushner’s phone and sends malicious code to a foreign dignitary. How can the US prove it wasn’t intentional? Equally as impactful, someone gets control of the phone and sends misinformation that compromises national security. This opens a whole can of worms about attribution and potential catastrophic international outcomes.
The Real Vulnerability: Humans
Look, I get it. I once worked for a global communications provider. The day I started, they issued me an already obsolete laptop and bare-bones phone. All I wanted to do was use my Linux laptop that I had at home and MY phone. It was easier. This is how shadow IT becomes a thing.
Using WhatsApp and personal phones for communication, especially among State Department staffers and other government dignitaries, is likely endemic to their institutional culture. The main reason is because it is easy, and WhatsApp is the communications tool of choice for most people in the world - especially outside the US.
That doesn’t make this behavior okay, and it definitely doesn’t make it safe for the country. It merely makes it convenient for the user.
I have a financial advisor. The SEC prohibits him from sending me any instant messages related to our financial dealings. He can’t use text, iMessage, WhatsApp or any other messaging app. The reason for his ban is because this is exactly how illicit financial deals get done, how fraud happens, how false promises are made. Shouldn’t we require a higher level of record-keeping and security for our government officials?
As always, the most difficult part of an effective security program is changing the human behavior. This is why phishing campaigns of all kinds continue to be effective despite our ever-growing cadre of information security defenses.
While WhatsApp is likely run as a company that takes privacy seriously, as they state, WhatsApp is still a company - a company made up of a lot of humans with a lot of access to a lot of useful data. It only takes one person to be compromised, make a mistake, or take improper action to create a catastrophic data incident.
This same concern applies to every enterprise
As an enterprise, the concerns around WhatsApp use applies to you, too. Last week we released a small blog entry on Facebom, a brute force tool for Facebook. (Which sadly may not be needed at all since Facebook left millions of users passwords exposed in clear text.) In that post, we discussed why these third-party messaging tools are risky for enterprise users. They are risky because of the illicit conversations and corporate data that can be traded. They are risky because of the opportunity for manipulation and data exfiltration. They are risky due to the fact that they are storing relevant data about your staff’s conversations.
The best path to managing risk from apps and services out of your direct control is through proper policies, thorough device management, aggressive content filtering, and monitoring of your cloud access broker services, all while keeping an eye out for data related to your organization in the wild.
GroupSense has paired intelligent technology with one of the best analyst teams in the world to help detect threats and data leaks for our enterprise and government clients. One of our key missions is protecting democracy through election monitoring. Our technology monitors millions of channels for fraud, account take-over, impersonation, electioneering, and disinformation campaigns. As part of our mission, we consult and train on intelligence risk, counter-intelligence, and the protection of key individuals in an organization. Tools like WhatsApp, Signal, and others provide promising security features, still, it is important to understand the trade-offs and implications of the use of these apps.
You may not be able to stop employees from violating policy. GroupSense is your last line of defense, identifying when your sensitive data is somewhere it shouldn’t be.







