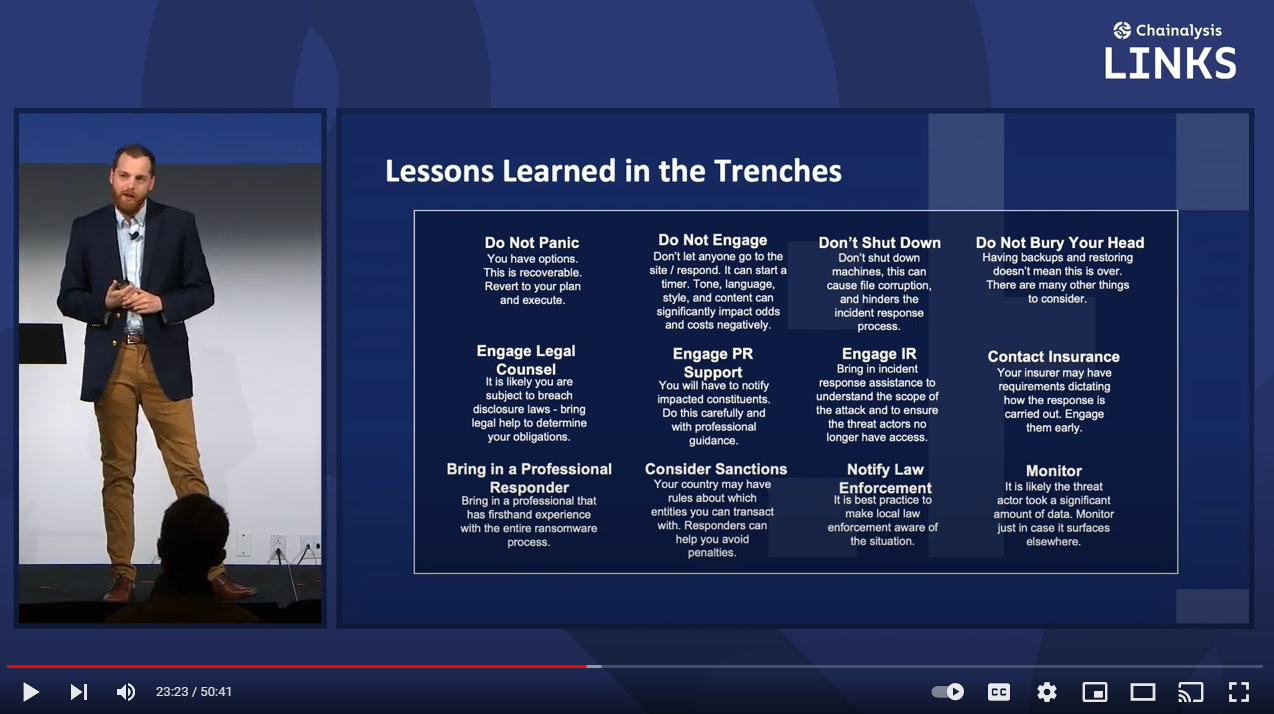
When faced with ransomware, revenue loss and damage to your organization’s reputation aren’t the only things to worry about. To reach the best-case scenario after an attack, your ransomware response team must understand how to talk to threat actors. With the right people on the team, you’re already off to a good start.
In today’s Ransomware-as-a-Service (RaaS) landscape, your organization is most likely dealing with highly specialized threat actors working within a larger business structure. For cybercriminals, this is a business deal. They will make common business trade-offs during negotiations if your team is skilled. Follow these instructions from GroupSense’s ransomware experts to get off on the right foot with the threat actor.
Avoid Confrontation
As in any other negotiation, your team should never engage in arguments with the threat actor. Though your team may feel anything but respect for cybercriminals, arguing with the threat actor will create a defensive environment that will decrease your chances of getting to the best-case outcome. Negotiators should be kind and professional during the proceedings.
Beyond avoiding confrontation, ransomware negotiators should display as much empathy as possible. Even though your organization is dealing with criminals, they most likely have a supervisor or manager expecting specific results watching over them. Displaying empathy can go a long way to getting your organization back on its feet.
Come Prepared
Through research and analysis, your team should understand all possible outcomes. An experienced negotiator will understand the pressure points on both sides and navigate them easily. Knowing your opponent will go a long way in any negotiation.
Your negotiator will have a leg up in the proceedings by understanding the ransomware landscape, common negotiation tactics, and even the ransomware group’s inner workings. Look for negotiators with years of experience in the space and success stories to share.
Word Choice Matters
Many ransomware groups operate outside of the US, and English may not be their first language. Be aware of how your words could be confusing or inflammatory. Instead, use language that is easy to understand, and always look at your words from the opponent’s perspective.
How you talk to threat actors is essential, but when you speak to them is just as critical. In a ransomware attack, every second matters. With so much on the line, GroupSense suggests hiring a third-party ransomware negotiator as soon as possible. Refer to your organization’s ransomware response plan to identify when you should bring in a negotiator. If you don’t have a response plan, get to writing one.
The ransomware negotiator should be the intermediary between you and the threat actor in this strategic role. Whether this individual is from a third-party or a part of your organization, the negotiator should have a specialized skillset in threat actor identification, profiling, negotiation, and dark web monitoring. In the early stages of the attack, the ransomware negotiator should determine which type of threat actor your organization is dealing with. This will inform the negotiator’s tactics.
Bringing in a skilled negotiator will also help you save significantly, as they know the value of what’s being held by the criminal, what their usual asking price is, and what the market will bear today. Skilled negotiators know whether the threat actor is typically willing to accept less money, knowing the ransom can be secured faster rather than waiting on a more significant payday, which comes with more considerable risk. Like in any negotiation, you never want to overpay. A savvy negotiator can also help you save money by ensuring lightning doesn’t strike twice. Supervising the recovery effort is critical to ensure there’s no malicious payload in the decryption keys; this can also thwart future extortion efforts by ensuring exfiltrated data is destroyed or recovered.
If you want more tips from GroupSense ransomware experts, download the Ransomware Negotiation Guide today.